A data analysis conducted by an outside research firm, and independently verified by BuzzFeed News, shows that Grindr, the popular gay dating app is sharing its users’ HIV status with two other companies. (Update: Late on Monday 2nd of April Grindr said it would stop sharing this information.)

The gay hookup app Grindr, which has more than 3.6 million daily active users across the world, has been providing its users’ HIV status to two other companies, BuzzFeed News has learned.
The two companies — Apptimize and Localytics, which help optimize apps — receive some of the information that Grindr users choose to include in their profiles, including their HIV status and “last tested date.”
Because the HIV information is sent together with users’ GPS data, phone ID, and email, it could identify specific users and their HIV status, according to Antoine Pultier, a researcher at the Norwegian nonprofit SINTEF. (SINTEF was commissioned to produce the report by Swedish public broadcaster SVT, which first publicized the findings.)
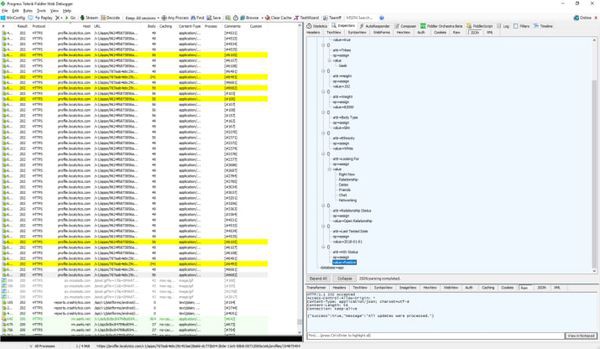
“The HIV status is linked to all the other information. That’s the main issue,” Pultier told BuzzFeed News. “I think this is the incompetence of some developers that just send everything, including HIV status.”
Grindr was founded in 2009 and has been increasingly branding itself as the go-to app for healthy hookups and gay cultural content. In December, the company launched an online magazine dedicated to cultural issues in the queer community. The app offers free ads for HIV-testing sites, and last week, it debuted an optional feature that would remind users to get tested for HIV every three to six months.
But the new analysis, confirmed by cybersecurity experts who analyzed SINTEF’s data and independently verified by BuzzFeed News, calls into question how seriously the company takes its users’ privacy.
“Grindr is a relatively unique place for openness about HIV status,” James Krellenstein, a member of AIDS advocacy group ACT UP New York, told BuzzFeed News.
“To then have that data shared with third parties that you weren’t explicitly notified about, and having that possibly threaten your health or safety — that is an extremely, extremely egregious breach of basic standards that we wouldn’t expect from a company that likes to brand itself as a supporter of the queer community.”
SINTEF’s analysis also showed that Grindr was sharing its users’ precise GPS position, “tribe” (meaning what gay subculture they identify with), sexuality, relationship status, ethnicity, and phone ID to other third-party advertising companies. And this information, unlike the HIV data, was sometimes shared via “plain text,” which can be easily hacked.
“It allows anybody who is running the network or who can monitor the network — such as a hacker or a criminal with a little bit of tech knowledge, or your ISP or your government — to see what your location is,” Cooper Quintin, senior staff technologist and security researcher at the Electronic Frontier Foundation, told BuzzFeed News.
“When you combine this with an app like Grindr that is primarily aimed at people who may be at risk — especially depending on the country they live in or depending on how homophobic the local populace is — this is an especially bad practice that can put their user safety at risk,” Quintin added.
Grindr said that the services they get from Apptimize and Localytics help make the app better.
“Thousands of companies use these highly-regarded platforms. These are standard practices in the mobile app ecosystem,” Grindr Chief Technology Officer Scott Chen told BuzzFeed News in a statement. “No Grindr user information is sold to third parties. We pay these software vendors to utilize their services.”
Apptimize and Localytics did not respond to requests for comment. Chen said that these companies will not share users’ data: “The limited information shared with these platforms is done under strict contractual terms that provide for the highest level of confidentiality, data security, and user privacy.”
Even so, security experts say, any arrangement with third parties makes sensitive information more vulnerable.
Read the full article from here

